Welcome to ProcDOT, a new way of visual malware analysis.
There are plenty of tools for behavioral malware analysis. The defacto standard ones, though, are Sysinternals’s Process Monitor (also known as
Procmon) and PCAP generating network sniffers like Windump, Tcpdump, Wireshark, and the like. These “two” tools cover almost everything a
malware analyst might be interested in when doing behavioral malware analysis.
But there’s a major problem with these tools. Any of them works in a so to say separated or isolated way, not knowing anything from each other.
Hence it’s kinda hard to get accordingly recorded activities together in one piece or picture. That’s where ProcDOT enters the stage. It fills this
actual gap by merging those records together.
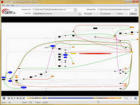
But ProcDOT does much more. It turns those thousands of monitored activities into a big behavioral picture - actually a graph - which can be
interactively explored making behavioral malware analysis as efficient as it never was before.
In this terms, regardless if you are already an expert in malware analysis or a beginner scratching on the latters surface, ProcDOT enables you to
•
Get an overall guts feeling for an entire situation within a glance,
•
Spot relevant parts and understand the correlation between them in minutes.
Features ...
•
Correlation of Procmon and PCAP data
•
Visualization as an interactive graph
•
Animation mode to easily understand timing aspects
•
Smart following algorithms to focus only relevant stuff
•
Detection and visualization of thread injection
•
Correlation of network activities and the causing processes
•
Activity time-line
•
Full text search and find of graph content also showing up in activity time-line
•
Filters to cleanup noise (global and session wise)
o
Support of various matching modes
▪
Full string match
▪
Heading string match
▪
Trailing string match
▪
Sub string match
▪
Regular expressions
o
Suppressing specific
▪
Registry keys
▪
Files
▪
Servers
•
Filter to match long and short paths
•
Graph content customization options
o
Show paths
o
Topical compression
o
Select which node/edge types (information) to show/suppress
•
Dumb mode if malware tries to play tricks on ProcDOT or if you just want to take a look at all running processes
•
Rich graph exporter supporting annotations
•
Fully fledged but still easy to use plugin engine
And after all: ProcDOT is absolutely free!
Welcome to ProcDOT.com

ProcDOT - Visual Malware Analysis Christian Wojner, 2022